San Diego CTF 2022 - OSINT - Mann Hunt
This was a really fun OSINT challenge that tasked us with finding someone based on nothing more than a username.
The challenge came with the following description…
“We were on the trail of a notorious hacker earlier this week, but they suddenly went dark, taking down all of their internet presence…All we have is a username. We need you to track down their personal email address! It will be in the form ****.sdctf@gmail.com. Once you find it, send them an email to demand the flag!”
Username: mann5549
First, let’s check the username with Sherlock –>
Since all we have is to go off of is a username, we need to leverage it to hone in a bit on our target and maybe some way to pivot onto another clue. The fastest way to get some groundwork laid is to search the username across a large variety of social media sites.
Doing that manually could take a large amount of time so we are going to automate this process with sherlock. To start digging around, we head over to our terminal and use python3 sherlock mann5549
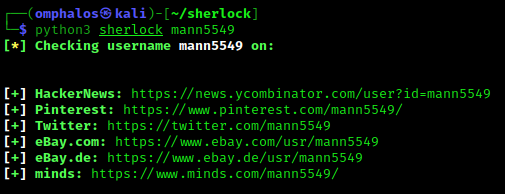
Sherlock is a script that takes the username we give it and it runs the name against 300 websites to determine if the username is found on any of the platforms it checked. After sherlock was done running the username it returns a small list of profiles with that username across a few various sites. This should narrow down our starting point significantly.
As this is a small list of links to go through, we can go ahead and check them out manually. We made our way through the list but stopped on the Twitter account as it caught our attention…
Twitter profile –>
We go ahead and check out a few of them and then we land on the Twitter profile. Immediately upon opening the profile, we can see that this users bio mentions how they set their Twitter account to private because people are after them.
There are no tweets here but there is here is a link to the users website.

Mann.codes website –>
Moving away from the Twitter profile, we head over to the website that was linked in the users Twitter profile. The homepage of the website doesn’t contain much other than a message telling us that the target knows who we are and that we will never find him.

Before trying anything else, we inspect the website from our Firefox browser by right clicking on the page and selecting Inspect. Within the <head></head> tags we can see that there is some useful metadata here. We can see a link to a github repository.

Pivoting to the Github repo –>
Following the link we found tucked away in the source code of the website, we end up on the Github repository owned by our target…

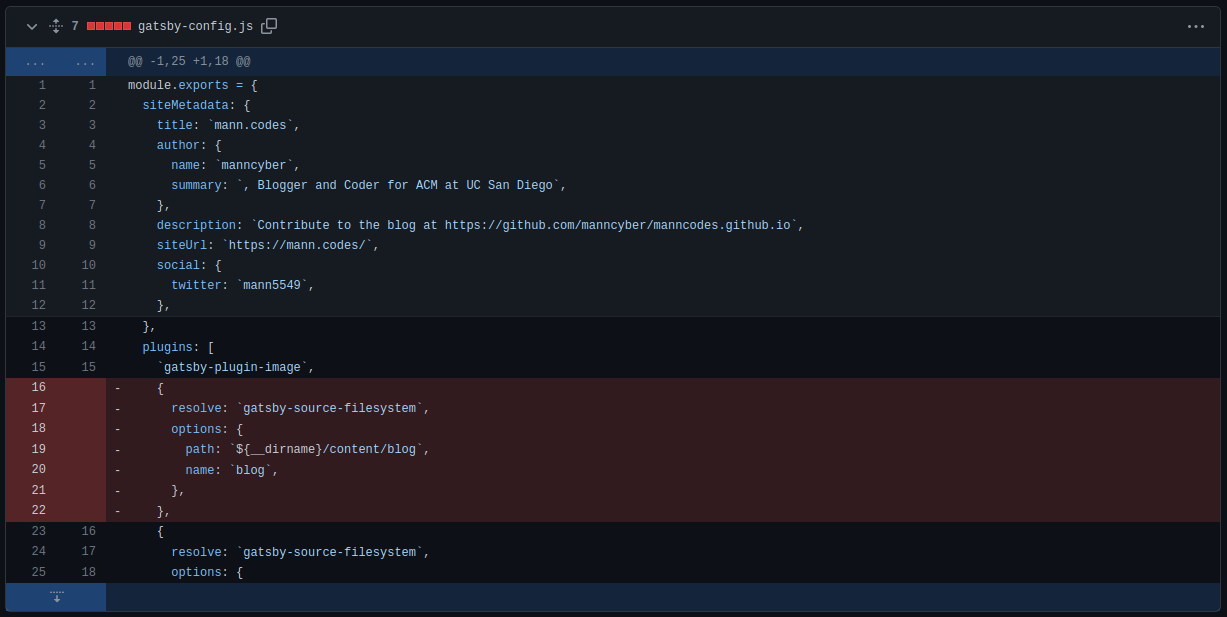
We can see that a couple of things have been deleted, again, due to our target knowing that they are being tracked down.
If we click on the description for the src folder we are taken to the page that shows us all of the commits made by our target. There are a total of 6 files here that have been changed. One of those is labeled gatsby-config.js:

If we expand this section to see further up the file, we find a summary that reads “Blogger and Coder for ACM at UC San Diego”.
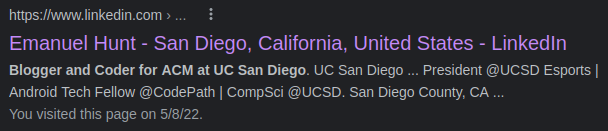
We decide to just keep it simple and put our amazing Google skills to work by searching for the phrase found in the target’s deleted file. The first result in the Google SERPs matches our query and it leads to a LinkedIn account for an Emanuel Hunt.
LinkedIn –>
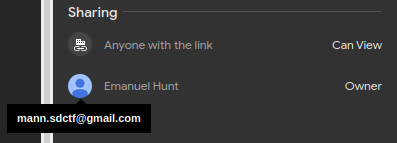
In the “About” section of our target’s LinkedIn page we are given a link to download his resume. We visit the link to look at his resume and notice that the email we need to retrieve has been replaced with asteriks.
Got the credentials & the flag –>

Luckily for us, in the right-hand panel under the sharing section we can hover over our targets profile and it displays their email address.
So, we send them an email to demand the flag back

And they responded back with the flag in the body of the email.
